
 |
 TV |
 A/V Receivers |
 Blu-ray/DVD |
 Computers |
 Cables |
 Routers |
| •
Internet
TV - video streaming • Routers - wireless how to setup network • How to buy a wireless router • How to setup wireless broadband internet • 100 Hookup Diagrams Routers A router is a device that forwards data packets along networks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP's network. Your home computer and video game form a LAN or local area network and the ISP is the other network. Routers are located at gateways, the places where two or more networks connect, and are the critical device that keeps data flowing between networks and keeps the networks connected to the Internet. When data is sent between locations on one network or from one network to a second network the data is always seen and sent to the proper location by the router. They accomplish this by using headers and forwarding tables to determine the best path for forwarding the data packets, and they use protocols such as ICMP to communicate with each other and configure the best route between any two hosts. The Internet itself is a global network connecting millions of computers and smaller networks and routers are used to get the data to the correct location. Why Would I Need a Router? For most home users, they may want to set-up a LAN (Local Area Network) or WLAN (wireless LAN) and connect all computers to the Internet without having to pay a full broadband subscription service to their ISP for each computer on the network. In many instances, an ISP will allow you to use a router and connect multiple computers to a single Internet connection. This is when home users will want to look at smaller routers, often called broadband routers that enable two or more computers to share an Internet connection.  What defines a router is not its shape, size or manufacturer, but its job function of routing data packets between computers. A cable modem which routes data between your PC and your ISP can be considered a router. In its most basic form, a router could simply be one of two computers connected together using ICS (Internet Connection Sharing). In this scenario, the computer that is connected to the Internet is acting as the router for the second computer to obtain its Internet connection. Often called broadband or Internet connection sharing routers, these routers allow you to share one Internet connection between multiple computers. Broadband wired routers are generally a small box-shaped hardware device with ports on the front or back into which you plug each computer, along with a port to plug in your broadband modem. These connection ports allow the router to do its job of routing the data packets between each of the the computers and the data going to and from the Internet. Depending on the type of modem and Internet connection you have, you could also choose a router with phone or fax machine ports. A wired Ethernet broadband router will typically have a built-in Ethernet switch to allow for expansion. These routers also support NAT (network address translation), which allows all of your computers to share a single IP address on the Internet. Internet connection sharing routers will also provide users with much needed features such as an SPI firewall or serve as a a DHCP Server. Going Wireless  Wireless broadband routers look much the same as a wired router, with the exception of possibly an antenna on top, and the lack of cable running from the computers to the router. Creating a wireless network adds a bit more security concerns as opposed to wired networks, but wireless broadband routers do have extra levels of embedded security. Along with the features found in wired routers, wireless routers also provide features relevant to wireless security such as Wi-Fi Protected Access (WPA) and wireless MAC address filtering. Additionally, most wireless routers can be configured for "invisible mode" so that your wireless network cannot be scanned by outside wireless clients. Wireless routers will often include ports for Ethernet connections as well. After a wireless network is established, you may possibly need to spend more time on monitoring and security than one would with a wired LAN.  Wired and wireless routers and the resulting network can claim pros and cons over each other, but they are somewhat equal overall in terms of function and performance. Both wired and wireless routers have high reliability and reasonably good security (without adding additional products). Generally, going wired will be cheaper overall, but setting up the router and cabling in the computers is a bit more difficult than setting up the wireless network. Of course, mobility on a wired system is very limited while wireless offers outstanding mobility features. 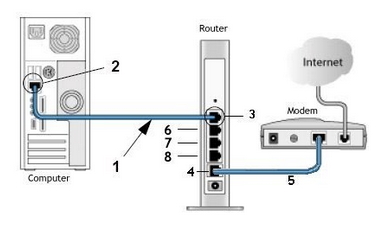 Computer hookup to modem for broadband internet 1) Ethernet cable 2) Ethernet RJ-45 jack 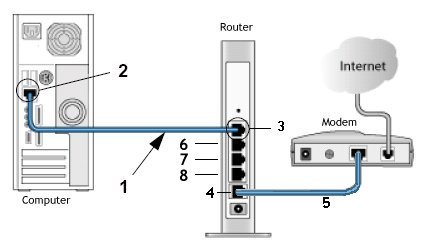 Computer hookup to router and router hookup to modem 1) Ethernet cable 2) Ethernet jack on computer 3) Ethernet jack on router 4) Router connection to modem 5) cable - router/modem communication 6) Additional port for video game 7) Additional port for device 8) Additional port for device 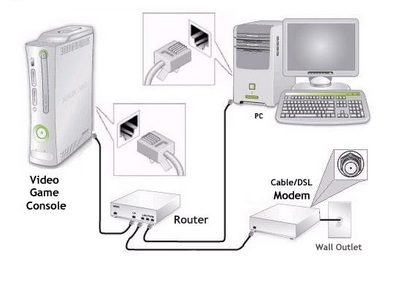 Router Hookup Diagram Single unit or MESH Routers Mesh routers are composed of multiple units, usually three, that are placed strategically around your home, where you need a good internet connection. One unit connects directly to your modem, then communicates wirelessly with the other two, creating a large “mesh” network to spread WiFi around your home more effectively. Wi-Fi 5 and Wi-Fi 6 - The need for speed - WiFi Standards Improvements over the years in speed and performance require new standards for devices. WiFi 6 - 802.11ax (released 2019) WiFi 5 - 802.11ac (released 2014) WiFi 4 - 802.11n (released 2009) WiFi 3 - 802.11g (released 2003) WiFi 2 - 802.11a (released 1999) WiFi 1 - 802.11b (released 1999)  Wi-Fi 6E - 6GHz band, yes a whole new band is available in 2020. Previous devices run in the 2.4GHz and the 5GHz bands. Yes, a new router and newer devices are required for 6E and they are expensive. Going into 2022 there are over 200 devices, over 70 laptops, 18 smartphones. Among routers and gateways, NETGEAR, Linksys, Asus, and TP-Link have all released Wi-Fi 6E models. Samsung and LG TVs - several models. Set Up a Network Router * broadband router configuration * home network setup How to set up a router for home computer networks Setup involves the physical connections of router to cable modem and router to computer(s) but also the logical setup and configurations of the router such as IP addresses, wireless security measures and SSID. Once the physical connections are completed, you can log on to the router from your computer and setup the router's internal configuration. 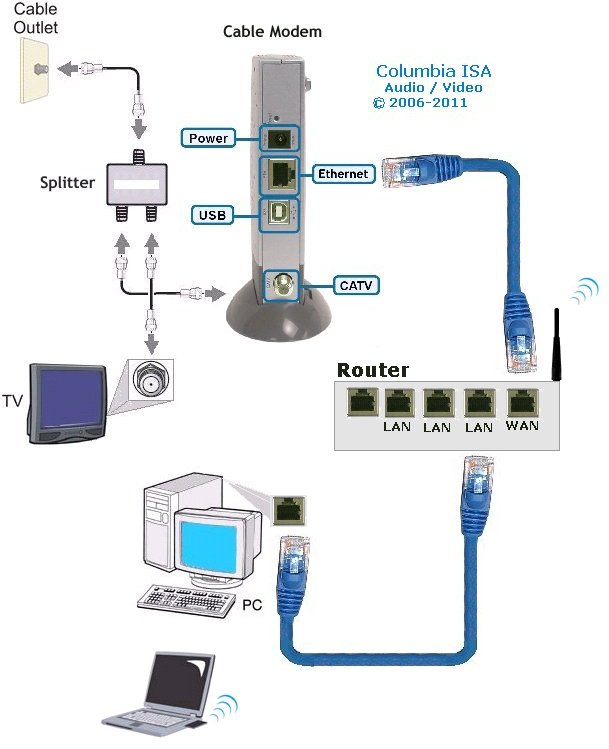 Plug in the router's electrical power cord, then turn on the router by pushing the power button.  This router is about the same size as your cable modem and costs about $70. Most network/cable modems connect via an Ethernet cable. The ethernet cable plugs into the router's rear jack named "WAN" or "uplink" or "Internet." After connecting the cable, be sure to power cycle (turn off and turn back on) the cable modem to ensure the router recognizes it.  Connect one computer to the router using an ethernet cable. Even if the router is a wireless model, connect this first computer to the router via a network cable. Using a cable during router installation ensures the maximum reliability of the equipment. Once a wireless router installation is complete, the computer can be changed over to a wireless connection if desired. Most routers have four RJ-45 ports to connect computers via an ethernet cable (LAN ports) and one RJ-45 port to connect the router to the cable modem (WAN port). Open the router's administration tool. From the computer connected to the router, first open your Web browser. Then enter the router's address for network administration in the Web address field and hit return to reach the router's home page. Routers are reached by their Web address "http://192.168.1.1" or "http://192.168.0.1" or "http://192.168.100.0" or something similiar. Consult your router's documentation to determine the exact address for your model. You do not need a working Internet connection for this step. IPCONFIG For Windows PCs click on START and RUN. Type in CMD and hit enter. In the window at the prompt, type ipconfig. 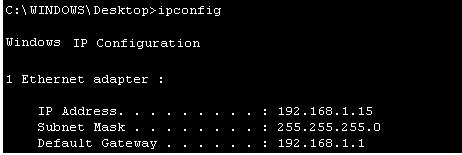 The IPCONFIG command or IPCONFIG/ALL shows you information about network devices such as IP addresses, and subnet mask. The Default Gateway IP address should be the address of the router. You enter this into your web browser address line to connect to the router. 1. First you need to connect the devices together. You need to connect your cable modem to the internet port on the back of the router, and the computer should go to one of the 4-ports on the router labeled Ethernet (1, 2, 3, 4). 2. Then turn on the cable modem first, wait for the lights to stabilize before powering on the router. Lights that you should have on the router are Power (solid green), Wireless/WLAN (Green sometimes flashing), One of the no. lights where the computer is plugged in (flashing), And the internet light (flashing). After doing this step you may be able to get online. If the internet will not work, you continue following step 3. 3. If the internet is still not working; we will need to adjust a setting on the router setup page. To access the setup page of the router you need to open your internet explorer or Firefox web browser on the computer that is hardwired directly to the router. In the address bar of your browser (Internet Explorer or Firefox) type http://192.168.1.1/ and hit enter or click Go. It will ask you for a username and password. Just type "admin" for the password field and there is no username. If you have run the setup CD prior to this, then use the password that you have set when you were running the setup CD. 4. Once you are in the setup page of your router make sure that the Internet Connection Type is set to Automatic Configuration DHCP, then click the save the settings button at the bottom of the page. After saving the settings, click the sub tab at the very top of the page that says MAC Address Clone. Set it to enable and click the button that will say Clone or Clone your PC's MAC address and save the settings again. 5. After doing step 4, do a power cycle. Power cycle is done by turning off the router, modem and computer. Leave them off for a minute, tuned them back on in this order. Cable Modem first, wait for the lights to stabilize, then the router, wait until the power light become solid. Then turn on the computer. This will get you online through the router. Log in to the router. The router's home page will ask you for a username and password. Both are provided in the router's documentation. You should change the router's password for security reasons, but do this after the installation is complete. If you want your router to connect to the Internet, you must enter Internet connection information into that section of the router's configuration (exact location varies). If using DSL Internet, you may need to enter the PPPoE username and password. Likewise, if you have been issued a static IP address by your provider (you would need to have requested it), the static IP fields (including network mask and gateway) given to you by the provider must also be setup in the router. Your provider may require you to update the MAC address of the router. If using a wireless router, change the network name (often called SSID). While the router comes to you with a network name set at the factory, you will never want to use this name on your own network. Verify the network connection is working between your one computer and the router. To do this, you must confirm that the computer has received IP address information from the router. Verify your one computer can connect to the Internet properly. Open your Web browser and visit a few Internet sites. Connect additional computers to the router as needed. If connecting wirelessly, ensure the network name (SSID) of each is computer matches that of the router. Finally, configure additional network security features as desired to guard your system. When using wireless, your radio signals can travel outside your house, allowing anyone with the proper gear to piggyback onto your network. But by using encryption, you can deter them from doing this. Encryption involves setting parameters in the router for data security. 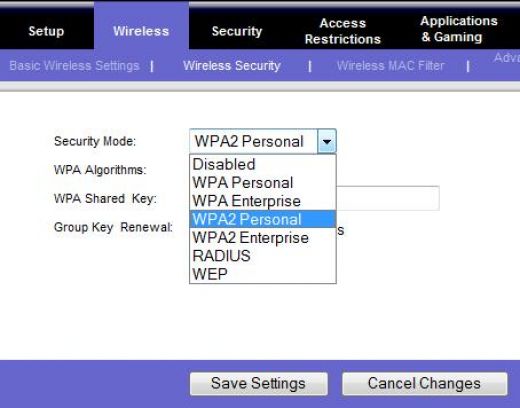 Wi-Fi Protected Access version 2 (WPA2) encryption. This is now showing up on a number of routers and is the current prefered method of data security and is worth the extra few steps involved to make sure your communications are secure. It is currently the best encryption method. How does WPA2 differ from earlier versions? First, it supports the 802.11i encryption standards that have been ratified by the IEEE. These are the commercial-grade encryption products that are available on enterprise-class products. Second, there are two encryption methods that WPA2 adds: one called Advanced Encryption Standard (AES) and one called Temporal Key Integrity Protocol (TKIP). Both of these allow for stronger encryption, and while the differences between the two aren't that important for our purposes, you should pick one method when you set up your network as you'll see in a moment. Finally, the protocol creates a new encryption key for each session, while the older encryption standards used the same key for everybody -- which is why they were a lot easier to crack. Also part of the new standard is Pairwise Master Key caching, where faster connections occur when a client goes back to a wireless access point to which the client already is authenticated. There is one more acronym I'll mention, and that is Pre-Shared Key or PSK. The WPA2 standard supports two different authentication mechanisms: one using standard RADIUS servers and the other with a shared key, similar to how WEP works. We'll get back to this in a moment, but let's show you how to get this train going. Step 1: Windows OS: First make sure your operating system is up to date. If you are running Windows XP, you'll need service pack 2 and you'll need to download the WPA2 patch that's located here. If you're using a Mac, you need to be running OS X 10.4.2 or better. Apple calls its version WPA2 Personal. Step 2: Wireless Adapter: While you are updating your Windows OS, you might want to make sure that the wireless adapter in your laptop is also up to the task of supporting WPA2. The Wi-Fi Alliance maintains an online database of products that is somewhat difficult to use. Go to their Web site, check the WPA2 box and then select which vendor you are interested in. If you have a built-in Intel wireless adapter, it needs to be running Intel's ProSet version 7.1.4 or better, excluding versions 8.x. You can get more information on Intel's Web site. Step 3: Wireless access point/router: Next, make sure your router/gateway can support WPA2. If you have purchased it in the last year, chances are good that it does, but you might need to update your firmware as well. Possibly update the firmware to the latest version. Wireless Encryption - WEP, WPA, and WPA2. Schemes for securing wireless communications under the 802.11 Wireles LAN (Local Area network) standard. * WEP - Wired Equivalent Privacy * WPA - Wi-Fi Protected Access * WPA2 - Wi-Fi Protected Access 2 In order to properly understand what WEP, WPA, and WPA2 are, we need to provide some background on what 802.11 is. About IEEE 802.11 IEEE (Institute of Electrical and Electronics Engineers) 802.11 is a set of standards specifying a means for wireless local area network (WLAN) communications using radio frequencies in the 2.4GHz, 3.6GHz, and 5GHz range. The most common modulation standards are the 802.11a, 802.11b, and 802.11g protocols--and now the more recent 802.11n. The 802.11a specification ammended the 802.11 standard to increase the raw transmission speed to 54Mbps at 5GHz band. The 802.11b specification ammended the 802.11 standard to increase the raw transmission speed to 11Mbps in the 2.4GHz band. Both 802.11a and 802.11b were ratifiedin 1999. The next modulation specification to ammend 802.11 was 802.11g. This allowed up to 54Mbps transmission rates at the 2.4GHz band. The more recent 802.11n specification was approved in September 2009, and allows up to 600Mbps raw transmission rates at the 2.4GHz or 5GHz range. Published October 2009. As you can see, the 802.11 standard is just a means of communication using modulation schemes over the airwaves, and as such, would need some form of security or privacy scheme to keep snoopers from reading what is being transmitted. What follow next are the three schemes to provide some form of secure communication over wireless transmission. WEP WEP was introduced in 1997. It was the first attempt at securing or providing confidentiality over wireless communications. In 2001, weaknesses in WEP were identified, and as a result, today WEP can be cracked within minutes. A few months after these discoveries, an ammendment called 802.11i was formed with the goal of solving this problem. The result was the introduction of the interim solution called WPA in 2003, then WPA2 later. WEP uses stream cipher RC4 for confidentiality and CRC-32 checksum for data integrity. IEEE depricated this specification in 2004. A standard 64-bit WEP uses a 40-bit key concatenated with a 24-bit block to produce a unique stream. At that time, 64-bit was a government limitation for exported encryption technology. Since then the limit was lifted allowing for the stronger 128-bit WEP (using 104-bit key). WPA and WPA2 Around the time the 802.11i task force was formed a solution was needed to keep the airwaves secure for LANs while a full recommendation was being formed through the 802.11i ammendment. WPA was an interim solution to the security flaws discovered in WEP. It implements most of what is found in the 802.11i specifications. It uses TKIP (Temporal Key Integrity Protocol) as the underlying security protocol which is based on RC4 (a stream cipher algorithm). TKIP uses many of the same mechanism as WEP, however through various means (e.g. message integrity check, per packet key hashing, broadcast key rotations, sequence counter) it is able to minimize its vulnerability. WPA2 is the final result of the work done under 802.11i, and it replaces WPA. WPA2 implements the mandatory components of 802.11i. It provides government grade security by implementing the National Institute of Standards and Technology (NIST) FIPS 140-2 compliant AES (Advanced Encryption Standard) encryption algorithm. There are two version of WPA2--the enterprise and personal versions. The personal version is also known as Pre-Shared Key mode. It is designed for home or locations where there is no need nor practical to have an authentication servers. It uses 256-bit key which can be entered as 64 HEX digits or as a passphrase of 8 to 63 ASCII characters. The enterprise version uses authentication servers and provides support for additional EAP (Extensible Authentication Protocol) types, in addition to EAP-TLS (Transport Layer Security). If you are concerned with communication privacy when communicating through the airwaves using your Wi-Fi device, then you'll want to stay away from WEP as it is the weakest of the three wireless security schemes. If WPA2 is supported by the wireless devices you are using, use WPA2. The next best option is WPA. Router manufacturers: APPLE • Apple Airport Extreme wireless router Best router For Mac or PC, share a printer, Simultaneous dual-band, 802.11n, Compatible with 802.11a/b/g. NETGEAR • Netgear wireless routers LINKSYS/CISCO • Linksys a division of Cisco Systems, Inc. is the global leader in Wireless and Ethernet networking for consumers. DSL - Digital Subscriber Line Columbia ISA Audio/Video Empowering consumers thru information |